As organizations embark on digital transformation and cloud migration, ensuring robust cloud security becomes paramount. Cloud security involves a set of procedures and technologies aimed at mitigating both external and internal threats to business security. This is especially crucial as businesses incorporate cloud-based tools and services into their infrastructure.
The terms "digital transformation" and "cloud migration" have become commonplace in enterprise discourse, each driven by the shared goal of instigating change. However, as organizations embrace these concepts to optimize their operational approach, a delicate balance between productivity and security must be maintained. While modern technologies offer expanded capabilities beyond on-premise infrastructure, transitioning primarily to cloud-based environments brings potential implications if not executed securely.
Achieving the right equilibrium necessitates a comprehensive understanding of how modern enterprises can leverage interconnected cloud technologies while implementing robust cloud security practices.
Why is Cloud Security important?
Cloud security is a shared responsibility between the provider and the customer, with distinct categories in the Shared Responsibility Model. These include provider-specific, customer-specific, and variable responsibilities based on the service model (IaaS, PaaS, SaaS). As organizations grapple with dynamic infrastructure management, as-a-service models offer relief by offloading time-consuming IT tasks.
Amidst the migration to the cloud, understanding security requirements for data protection is crucial. While cloud providers prioritize server integrity, data asset security remains the responsibility of organizations. Evolving security threats, targeting cloud providers, demand proactive measures to mitigate governance and compliance risks tied to client information.
Regardless of enterprise size, cloud security is a vital discussion. As cloud infrastructure underpins modern computing across industries, effective adoption hinges on robust security measures. Whether in a public, private, or hybrid cloud setting, implementing security solutions and best practices is imperative for ensuring business continuity.
What are top Cloud Security challenges?
The absence of clear perimeters in the public cloud introduces a distinct security reality, particularly with the adoption of modern cloud approaches like CI/CD methods, serverless architectures, and ephemeral assets. Key cloud security challenges faced by today's cloud-oriented organizations include:
- Increased Attack Surface: The public cloud environment becomes an attractive attack surface exploited by hackers targeting poorly secured cloud ingress ports, leading to disruptive threats like malware, Zero-Day attacks, and Account Takeover.
- Lack of Visibility and Tracking: In the IaaS model, cloud providers maintain full control over the infrastructure layer, limiting customer visibility. This lack of visibility extends to PaaS and SaaS cloud models, hindering the effective identification and quantification of cloud assets.
- Ever-Changing Workloads: Dynamic provisioning and decommissioning of cloud assets at scale and velocity pose challenges for traditional security tools, incapable of enforcing protection policies in such a flexible and dynamic environment with constantly changing and ephemeral workloads.
- DevOps, DevSecOps, and Automation: Organizations embracing the highly automated DevOps CI/CD culture must embed appropriate security controls in code and templates early in the development cycle. Implementing security-related changes post-deployment can undermine the organization's security posture and lengthen time to market.
- Granular Privilege and Key Management: Loosely configured cloud user roles often grant extensive privileges, risking security. Improperly configured keys and privileges at the application level expose sessions to security risks.
- Complex Environments: Consistently managing security in hybrid and multi-cloud environments requires seamless methods and tools across public and private cloud providers and on-premise deployments, including branch office edge protection for geographically distributed organizations.
- Cloud Compliance and Governance: While leading cloud providers align with international (PCI-DSS, ISO 27001/27017/27018) and local standards (Decree 53/2022/ND-CP, Decree 13/2023/ND-CP), customers are responsible for ensuring compliance. The challenges of poor visibility and dynamic cloud environments make the compliance audit process difficult, necessitating tools for continuous compliance checks and real-time alerts about misconfigurations.
- Access Management and Shadow IT: Administering access points in cloud environments is challenging, particularly without strict BYOD policies, posing risks for unfiltered access from any device or geolocation.
- Misconfigurations: Inadvertent insider threats in cloud computing environments result from misconfigured assets, accounting for a significant percentage of breached records. Misconfigurations include leaving default administrative passwords or neglecting appropriate privacy settings.
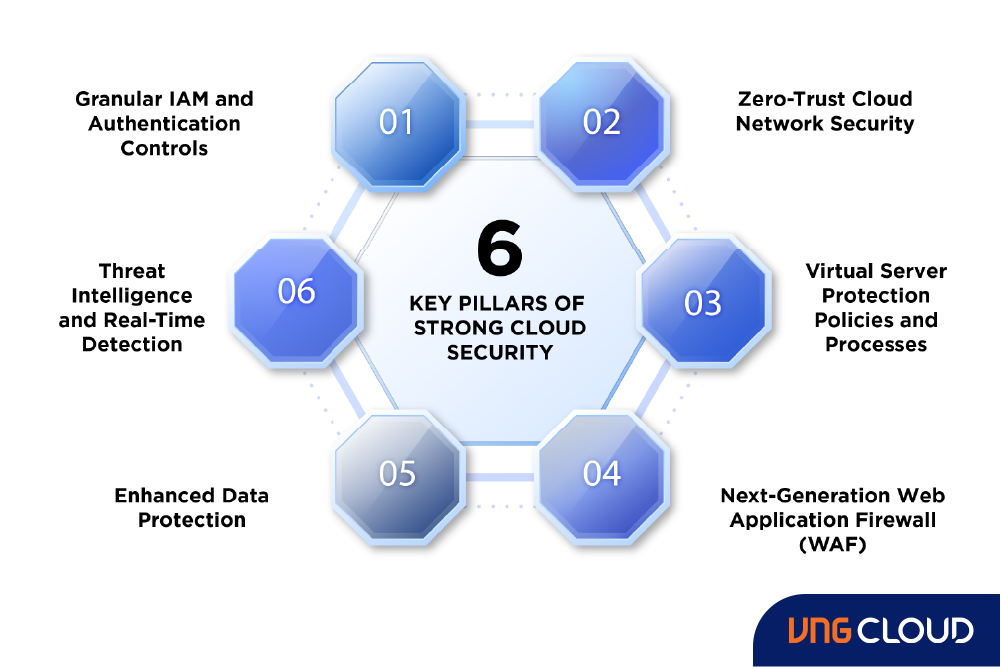
Key Pillars of Strong Cloud Security
While leading cloud providers like AWS, Google Cloud, VNG Cloud often offer a range of cloud-native security features, it's crucial to supplement these with third-party solutions for achieving enterprise-grade protection against breaches, data leaks, and targeted attacks. An integrated cloud-native/third-party security stack is essential to provide centralized visibility and policy-based granular control, aligning with industry best practices:
- Granular IAM and Authentication Controls: Implement granular, policy-based Identity and Access Management (IAM) controls across complex infrastructures. Work with groups and roles, facilitating easier IAM definition updates based on evolving business requirements. Enforce minimal access privileges, employ strong IAM hygiene with policies like password strength, and implement permission time-outs.
- Zero-Trust Cloud Network Security: Deploy business-critical resources in logically isolated sections, such as Virtual Private Clouds (VPC). Use subnets for micro-segmentation, applying granular security policies at subnet gateways. Employ dedicated WAN links in hybrid architectures and configure static user-defined routing for customized access.
- Virtual Server Protection Policies and Processes: Leverage robust Cloud Security Posture Management (CSPM) for consistent governance and compliance rule application during virtual server provisioning. Audit configuration deviations and automate remediation where possible, incorporating processes like change management and software updates.
- Next-Generation Web Application Firewall (WAF): Safeguard all applications, especially cloud-native distributed apps, with a next-generation WAF. Granularly inspect and control traffic to and from web application servers, automatically update WAF rules based on traffic behavior changes, and deploy closer to microservices running workloads.
- Enhanced Data Protection: Implement enhanced data protection practices, including encryption at all transport layers, secure file shares, continuous compliance risk management, and maintaining data storage hygiene. Detect and terminate misconfigured buckets and orphan resources.
- Threat Intelligence and Real-Time Detection: Use third-party cloud security solutions for threat intelligence that detects and remediates known and unknown threats in real-time. Aggregate cloud-native logs and cross-reference with internal and external data sources. Leverage AI-based anomaly detection for unknown threats, followed by forensics analysis and real-time alerts on intrusions and policy violations for swift remediation.
4 Common Types of Cloud Security Solutions
- Identity and Access Management (IAM): IAM tools and services enable enterprises to enforce policy-driven protocols for user access, encompassing both on-premises and cloud-based services. IAM's core functionality involves creating digital identities for users, actively monitoring, and imposing restrictions during data interactions.
- Data Loss Prevention (DLP): DLP services offer tools designed to secure regulated cloud data. Utilizing remediation alerts, data encryption, and other preventive measures, DLP solutions protect stored data, whether at rest or in motion.
- Security Information and Event Management (SIEM): SIEM provides a comprehensive security orchestration solution automating threat monitoring, detection, and response in cloud-based environments. Leveraging AI-driven technologies for correlating log data across platforms, SIEM empowers IT teams to apply network security protocols and respond rapidly to potential threats.
- Business Continuity and Disaster Recovery: Despite preventative measures, data breaches and disruptive outages can occur. Business continuity and disaster recovery solutions are crucial in cloud security, providing organizations with tools, services, and protocols to expedite data recovery and resume normal business operations in the event of vulnerabilities or system outages.
How to Approach Cloud Security?
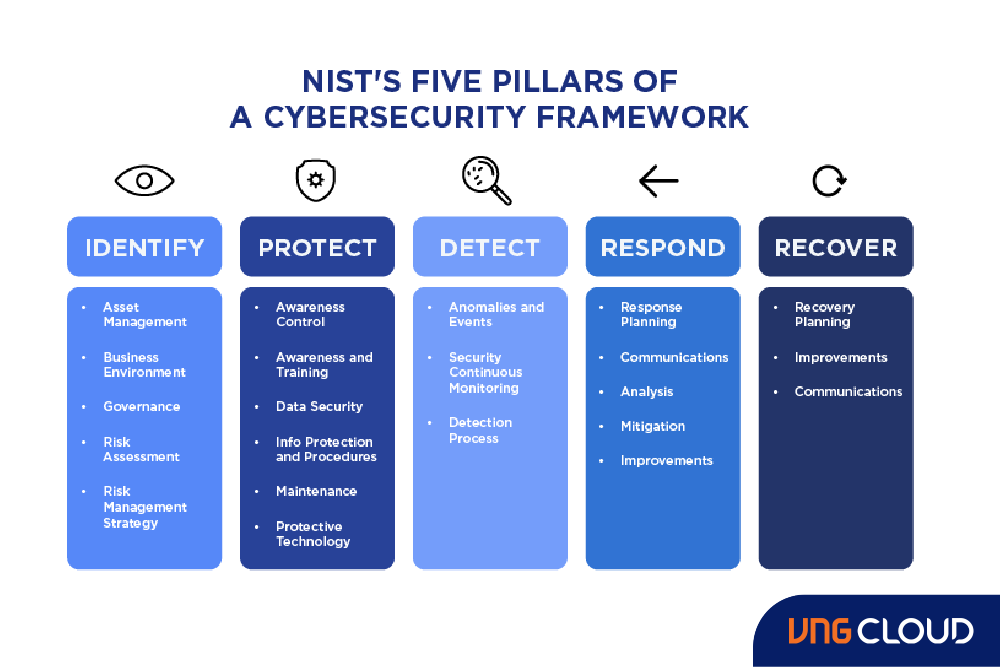
Securing the cloud varies for each organization and depends on multiple factors. However, the National Institute of Standards and Technology (NIST) has outlined a set of best practices to establish a secure and sustainable cloud computing framework.
NIST's recommended steps guide organizations in self-assessing their security readiness and implementing appropriate preventive and recovery security measures. These principles align with NIST's five pillars of a cybersecurity framework: Identify, Protect, Detect, Respond, and Recover.
A cutting-edge technology supporting the implementation of NIST's cybersecurity framework is Cloud Security Posture Management (CSPM). CSPM solutions address a prevalent issue in many cloud environments - misconfigurations. Cloud infrastructures left misconfigured, whether by enterprises or cloud providers, can introduce vulnerabilities that significantly expand an organization's attack surface. CSPM tackles these challenges by facilitating the organization and deployment of key cloud security components, including Identity and Access Management (IAM), regulatory compliance management, traffic monitoring, threat response, risk mitigation, and digital asset management.
Embracing Zero Trust in Cloud Security
The concept of Zero Trust, introduced by John Kindervag in 2010, revolutionizes cloud security by challenging the traditional approach of automatically trusting entities within or outside the network. Instead, Zero Trust advocates for a continuous verification process—authorizing, inspecting, and securing everything.
Zero Trust emphasizes a least privilege governance strategy, restricting user access to only the resources essential for their tasks. It also encourages developers to diligently secure web-facing applications. For instance, neglecting consistent port blocking or implementing unnecessary permissions can leave applications vulnerable to hackers, allowing unauthorized access to databases.
Furthermore, Zero Trust networks employ micro-segmentation to enhance the granularity of cloud network security. By creating secure zones in data centers and cloud deployments, micro-segmentation isolates workloads, secures content within each zone, and applies policies to safeguard traffic between zones.
VNG Cloud's commitment to security aligns with industry best practices, offering a range of solutions to address diverse challenges. Whether it's leveraging advanced threat detection, implementing zero-trust principles, or ensuring compliance with regulatory standards, we stand as a reliable ally in fortifying your cloud infrastructure.